How to Avoid Crypto Scams in 2025
Learn how to recognize and protect yourself from common crypto scams like rug pulls, fake wallets, phishing, Ponzi schemes and more. Stay safe in Web3.

Let's be honest: the crypto space is exciting, full of innovation, and for many, full of hope. But it's also a goldmine for scammers. And while some traps are easy to spot, others are incredibly sophisticated, designed to trick even the most careful users. If you're holding crypto or planning to invest, knowing how these scams work is not just helpful—it's essential.
With the rise of digital currencies has come an explosion of fraudulent activity. From shady airdrops to dodgy wallets and fake projects promising impossible returns, the tricks have evolved. They play on urgency, hype, and a lack of regulation. So, what can you do about it?
Let's go through the most common scams and, more importantly, how to stay away from them.
Airdrops That Aren't What They Seem
Airdrops are popular in crypto—projects give away tokens to build buzz or reward early users. But that goodwill has been hijacked. Some airdrops are just bait to collect your private keys or trick you into downloading malware. They'll promise free tokens in exchange for a small fee or ask you to connect your wallet to a suspicious-looking site. Once you do, you might have just handed over access to your funds.
Be wary of any airdrop that demands sensitive info, especially seed phrases. No real project will ever ask for those.
The Classic Rug Pull
This one's sadly common. Developers launch a shiny new token, maybe with some flashy marketing or a slick website. Early investors jump in, hoping it's the next big thing. Then, just when the price starts to climb, the devs pull all the liquidity out and vanish. Your tokens? Now worth next to nothing.
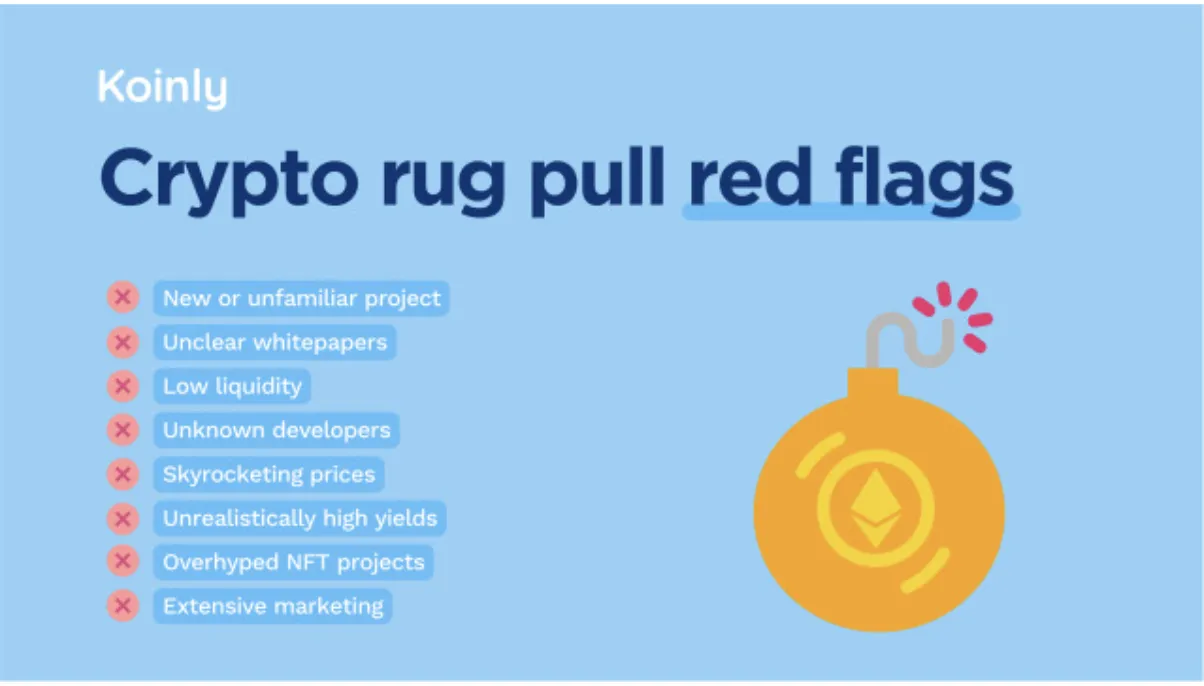
These scams often play out fast. Everything looks legit… until it doesn't. If the team behind a project is anonymous or the smart contract isn't verified, you're playing with fire.
The Old Ponzi in New Clothes
If something offers consistent, high returns with little risk, and it sounds too good to be true, it probably is. Many of these setups are just Ponzi schemes in disguise. They pay early users with the money from new ones. Eventually, it collapses. The ones who got in early may walk away with profits, but the rest? Left holding the bag.

These scams often pressure you to bring in new people. The moment a "project" needs constant recruitment to survive, that's your red flag.
Fake Wallets with a Familiar Face
You download a wallet app that looks exactly like MetaMask or Trust Wallet. The logo's there, the interface feels right… but it's a trap. You enter your seed phrase and, poof, your assets are gone. Fake wallet apps are sneaky. They often pop up in app stores or get shared in Telegram groups. Even some QR codes at events have been rigged to link to fake downloads.
Double check you're using official sources. It only takes one wrong download to lose everything.
ICO Hype Machines
Initial Coin Offerings (ICOs) were all the rage during crypto's early years. They've died down since, but scammy ones still pop up. The pitch is usually the same: invest now in a revolutionary idea and get in early. You're promised tokens, profits, access. But after the money's raised, the team disappears or the project just doesn't materialize.
If the team doesn't have a track record, there's no whitepaper, or the roadmap is vague… it's a no from me.
Whale Games and Price Manipulation
Big players, often called whales, can shake the market just by moving large sums. Some do it strategically, pumping a token's price to attract retail buyers, only to dump it when the price spikes. The crash leaves smaller investors rekt. Others might trigger sudden dips just to scoop up tokens on the cheap.
It's not always illegal, but it's shady. If you're following hype without understanding the project, you might be their exit liquidity.
Burn Events That Burn You
Burning tokens—destroying a portion of supply—is sometimes used by projects to create scarcity. But scammers have twisted this too. They'll pretend you need to send tokens to an address to "participate" in a burn event that will multiply your assets. Spoiler: you won't get anything back.
Legit burns are done by the project itself and don't require your direct involvement. Be suspicious of any unsolicited instructions involving your funds.
Man-in-the-Middle Attacks
Imagine you're about to send some crypto. You copy-paste the recipient's wallet address, double-check it… and hit send. Except, somewhere between copying and pasting, a hidden malware swapped it for a scammer's address. This is a man-in-the-middle (MITM) attack. These scams work silently, often through compromised Wi-Fi or dodgy browser extensions.
Security tips:
Avoid using public Wi-Fi for anything crypto-related
Use hardware wallets when possible
Enable 2FA everywhere
Keep your system clean of malware
Cryptojacking: Mining Without Consent
Some scams don't even steal your coins—they steal your computer power. Cryptojacking is when a hacker secretly uses your device to mine crypto. Your laptop runs hot, your battery drains quickly, and your CPU is working overtime. You might not even realize it's happening.
Run antivirus software regularly. If your machine is slowing down for no clear reason, it's worth checking.
Address Poisoning: A Subtle Threat
Ever sent crypto to the wrong address? Scammers know how common that is. With address poisoning, they send you tiny transactions from a wallet address that looks nearly identical to one you've used before. Later, when you go to send funds and copy the wrong one from your history… you send it straight to them.
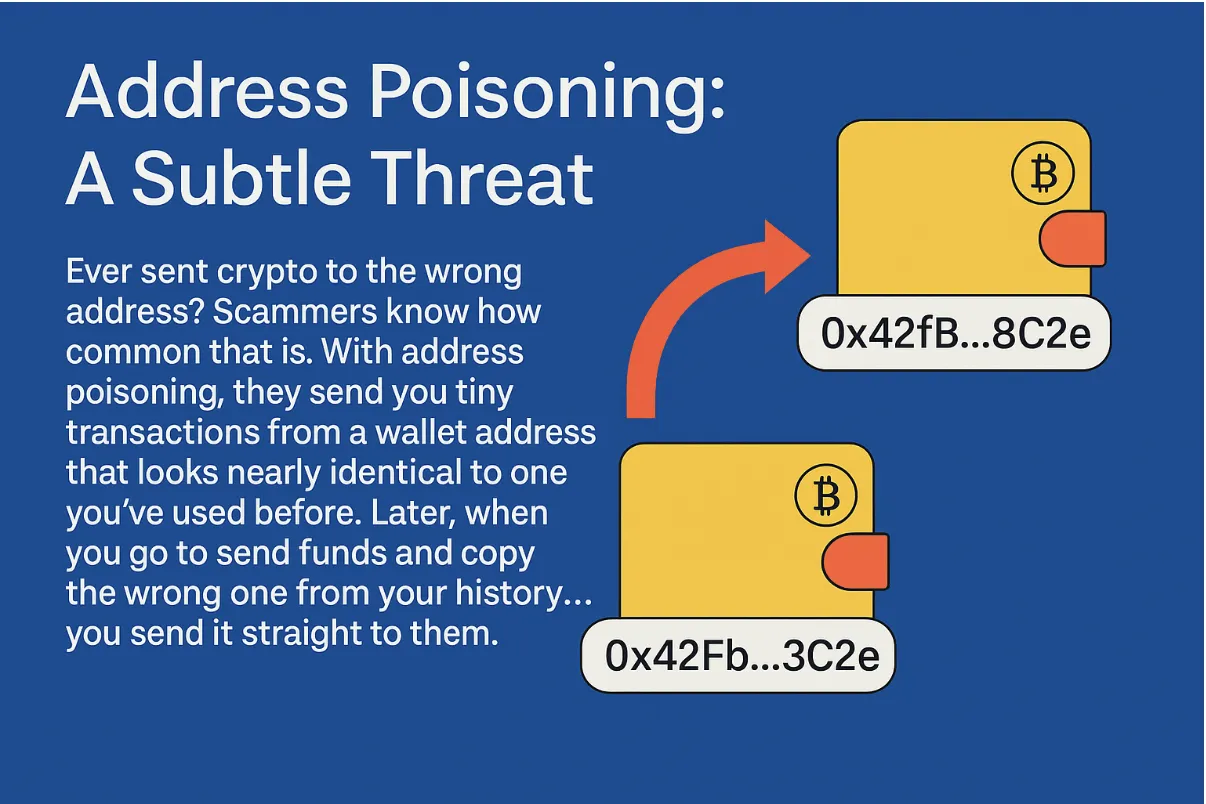
Always triple-check the full address, especially the first and last few characters. Better yet, use saved contacts or QR codes when possible.
If You've Been Scammed, Here's What to Do
First, breathe. It's devastating, yes, but it happens to even the most careful users.
Immediate Steps:
Stop all contact with the scammers—don't try to negotiate or get revenge
Secure remaining assets—move funds to a new wallet, change passwords
Enable 2FA everywhere you haven't already
Report the scam to platforms involved and local authorities if possible
Some blockchains let you track where funds went, but recovery is rare. Stay vigilant and keep learning.
Red Flags to Watch For
Guaranteed high returns with little to no risk
Pressure to act quickly or "limited time offers"
Requests for seed phrases or private keys
Anonymous teams with no track record
Unverified smart contracts or suspicious code
Heavy recruitment focus rather than product development
Professional-looking websites with no substance behind them
Final Thoughts
The crypto space is growing fast, and with that growth comes risk. Scams are evolving, but the basics remain the same: if it sounds too good to be true, if someone's rushing you, or if you're being asked for something that doesn't feel right, take a step back.
Key principles for staying safe:
Use official channels only
Question everything
Never share your seed phrase
Do your own research (DYOR)
Start small with new projects
Trust your instincts
The best defense in crypto? It's not a shiny tool or a new protocol—it's knowledge. Stay sharp, stay curious, and don't let scammers win.
Never Miss Daily Alpha!
Get the latest crypto insights, market analysis, and exclusive tips delivered straight to your inbox daily.
Subscribe to Our Newsletter